What is Post-Quantum Cryptography?








Encrypted emails from your bank, your online shopping transactions and social media messages — all of which could soon be at risk. The development of quantum computers is ushering in a quiet but profound revolution in the world of cybersecurity. These next-generation machines will have the capacity to decode existing encryption systems in seconds.
This is where post-quantum cryptography comes into play. This innovative security approach uses math problems that are resistant to both today's computers and the quantum machines of the future. NIST, America's leading technology agency, published the first post-quantum standards in 2024, accelerating the process of renewing digital security infrastructures around the world.
In this article, we will examine the basic functioning of post-quantum cryptography, how it will affect which industries, and how organizations should prepare for this transformation.
Post-quantum cryptography is the process of developing encryption algorithms and cryptographic systems designed to be secure against both classical and quantum computers. This approach aims to ensure digital security in the future, where it is predicted that it can crack existing encryption methods by harnessing the power of quantum computing.
Traditional cryptography systems are built on mathematical difficulties such as the division of large numbers into prime multipliers, the discrete logarithm problem or the elliptic curve discrete logarithm problem. Although these problems are complex for classical computers that will take billions of years to solve, quantum computers can solve these problems in a relatively short time using the Shor algorithm.
Post-quantum cryptography, on the other hand, uses different mathematical foundations. Preference is given to mathematical structures in which even quantum computers will be challenged, such as lattice (lattice) -based problems, hash functions, error-correcting codes, and multivariate polynomial equations. These algorithms can work on current classical computers and demonstrate resilience against future quantum threats.
An important point is that a quantum computer is not needed to use post-quantum cryptography. These algorithms provide protection against future quantum attacks, while running smoothly on the traditional computers we use today.
The threat that quantum computers bring to the world of cryptography is made concrete by the algorithm developed by Peter Shor in 1994. The Shor algorithm gives the ability to solve the problem of splitting large numbers into prime multipliers in quantum computers at exponential speed. This situation directly threatens widely used asymmetric encryption systems such as RSA, DSA, and ECDSA.
According to the Global Risk Institute's 2024 report, nearly half of experts in developing cryptographically relevant quantum computers (CRQC) believe that such a system could be realized with at least a 5% probability by 2033. More than a quarter of experts see this probability as 50% or higher.
In the current state, quantum computers are not yet capable of breaking cryptographic systems. But the attack pattern called “harvest now, decrypt later” is of great concern. In this model, attackers plan to decrypt this data when they gain access to powerful quantum computers in the future by storing encrypted data that they cannot decrypt at the moment.
Therefore, regardless of when exactly quantum computers will be ready, it is critical to strengthen digital security systems already. Historically, the transition process should begin as soon as possible, since full integration of new cryptographic infrastructures takes 10-20 years.
The United States National Institute of Standards and Technology (NIST) has published the first three final standards, completing the post-quantum cryptography standardization project it launched in 2016 in 2024. These standards represent the result of eight years of intensive work by the global cryptography community.
FIPS 203 (ML-CREAM)This standard, called Module-Lattice-Based Key-Encapsulation Mechanism, was designed as the primary algorithm for general encryption. Derived from the Crystals-Kyber algorithm, ML-KEM offers relatively small encryption keys and fast processing capability. Optimized for secure key exchange between two parties.
FIPS-204 (ML-DSA)Module-Lattice-Based Digital Signature Algorithm is a digital signature standard developed from Crystals-Dilithium. This algorithm for authentication and data integrity is based on lattice-based math problems.
FIPS-205 (SLH-DSA)Stateless Hash-Based Digital Signature Algorithm is derived from the SPHINCS+ algorithm. Based on hash functions, this system offers stateless digital signature solutions and provides long-term security.
In March 2025, NIST announced that it had chosen HQC (Hamming Quasi-Cyclic) as its fifth algorithm. This algorithm is positioned as the fallback standard for ML-KEM and uses a different code-based mathematical approach. The HQC standard is expected to be completed in 2027.
These algorithms are based on the complex mathematics of polynomial lattices and hash functions. Even for the most powerful quantum computers, breaking these systems will be a daunting task.
Post-quantum cryptography adopts different mathematical approaches that are resistant to quantum computers. Each approach offers its own unique advantages and areas of application.
Lattice Based Cryptography: Lattice-based systems, one of the most popular post-quantum approaches, are based on the difficulty of the problem of finding the shortest vector in multidimensional lattice structures. Two of the NIST standards (ML-KEM and ML-DSA) use this approach. Although lattice algorithms have the advantage of being able to process faster than existing systems, their key sizes are larger than traditional methods.
Hash Based Digital Signatures: Using Merkle trees and single-use signature schemes, this method relies on the security of hash functions. The SLH-DSA standard represents this category. Hash-based systems provide long-term security and have proven resistance to quantum attacks.
Code-Based Encryption: Using the complexity of error correction codes, this approach includes the McEliece and Niederreiter encryption systems. The original McEliece system, analyzed for more than 40 years, has proven its reliability. The HQC algorithm also falls into this category.
Multivariate Cryptography: Based on the difficulty of solving multivariate systems of polynomial equations, this method is used especially in digital signature applications. Although it offers small signature sizes, key sizes are usually large.
Each approach offers different performance characteristics, safety levels, and application requirements. This diversity allows choosing the most suitable solution for different use scenarios.
Post-quantum cryptography has applications of critical importance in a variety of industries. Each industry adopts different post-quantum solutions to meet its unique security requirements.
Financial Services: The banking sector prioritizes post-quantum algorithms for the protection of customer data and the security of financial transactions. Online banking, credit card transactions and cryptocurrency transfers require encryption that is resistant to the quantum threat. Financial institutions aim to upgrade their critical systems to post-quantum standards by 2026.
telecommunication5G and future 6G networks integrate post-quantum security protocols. Mobile communication, internet infrastructure and IoT Connections between devices must be protected against future quantum attacks. Telecommunications operators are testing ML-KEM and ML-DSA algorithms to ensure network security.
Health Sector: Patient records, medical imaging data and telemedicine applications include sensitive personal information. HIPAA compliance and patient privacy require post-quantum encryption. Hospitals and health technology companies are implementing new standards to protect electronic health records.
Government Agencies and Critical InfrastructuresNational security, protection of energy grids, transport systems and water resources are vital. The U.S. Agency for Cybersecurity and Infrastructure Security (CISA) requires federal agencies to complete the post-quantum transition by 2035. Critical infrastructure providers are preparing emergency transition plans.
The transition to post-quantum cryptography is a complex process that requires extensive planning and coordination. Organizations must identify which cryptographic algorithms are being used by analyzing their existing systems and determine migration priorities.
Technical challenges include larger key sizes and different performance characteristics of the new algorithms. Existing hardware and software systems must be updated or modified to support post-quantum algorithms. Network protocols, database encryption systems, and APIs must be restructured.
The European Union is proposing that member states begin the transition to post-quantum cryptography by the end of 2026. The United States has set a 2035 target for federal agencies. Private sector organizations must establish their own timelines based on risk assessments.
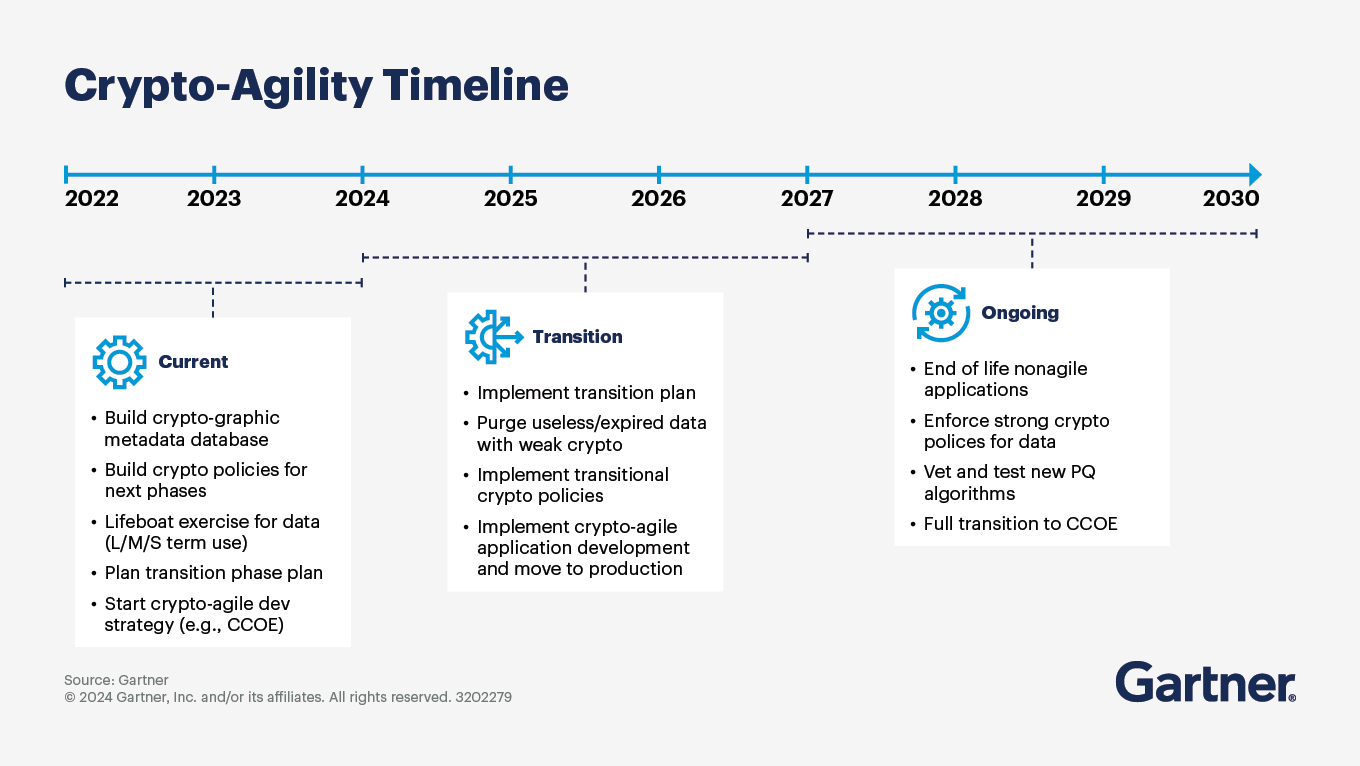
The concept of crypto agility is important for preparing for future algorithm changes. Systems should be designed in such a way that they can easily integrate new cryptographic algorithms. This approach provides the ability to react quickly to possible vulnerabilities in the future.
Post-quantum cryptography is a critical area of technology shaping the future of digital security. The standards, published by NIST in 2024, constitute concrete steps in the preparedness process for the quantum threat. ML-KEM, ML-DSA and SLH-DSA algorithms provide reliable solutions for different application areas.
Organizations need to act already for a successful transition. Risk assessment, system inventory, and transition planning must be completed before the quantum threat materializes. Post-quantum cryptography is not just a technological update, but a strategic investment that guarantees the secure future of our digital society.
In order for natural language processing (NLP) and artificial intelligence models to make sense of texts, they need to be broken down into smaller units. This process is called tokenization.
Regression metrics are mathematical indicators that measure the success of machine learning models in numerical value predictions. These metrics allow performance evaluation by quantitatively expressing the difference between the model's predictions and the actual data.
Hybrid Cloud Computing is a cloud computing model in which enterprises take advantage of the advantages of both models by using a combination of private cloud and public cloud infrastructures.

We work with leading companies in the field of Turkey by developing more than 200 successful projects with more than 120 leading companies in the sector.
Take your place among our successful business partners.
Fill out the form so that our solution consultants can reach you as quickly as possible.
